Posted by Rick Davidson
IT Infrastructure and Operations Still Matter [White Paper]
Nearly all emerging technologies have followed a normal lifecycle. This lifecycle usually starts with a unique technology innovation coming to market, then moves to inflated expectations as the promised value of the technology exceeds reality, followed by disappointment as expectations are dashed. It then moves into a period of awakening as a true understanding of…
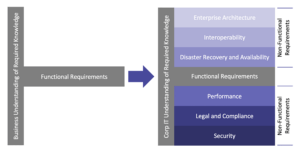
The Whole Picture: Functional Requirements Are Important, But Not Sufficient in Selecting Software
If you are a business leader, are you frustrated with an IT organization that gives you all the reasons why your purchase of a software application won’t work versus figuring out how to make it work? If you are an IT leader, do you find your concerns about application security, performance, compliance and a slew…
Tags: Guided Autonomy, Shadow IT, Software-as-a-Service (SaaS)
Guided Autonomy Governance Model [White Paper]
Over the past several years, the tension has grown between corporate IT and the departments it serves throughout the organization. This tension exists for many reasons, but is escalating as departments are increasingly acquiring their own technology to meet their specific business needs. Corporate IT departments often refer to this as “Shadow IT.” While the…
Tags: Business Agility, Business Optimization, IT Performance Improvement
Why Now is the Time for Business Agility
Many business leaders today face the challenge of transforming their organizations to compete in a world that is defined by increasing levels of uncertainty, chaos and complexity. A global pandemic, social justice concerns, rapidly evolving customer expectations, the changing nature of work – these and other factors are driving the need to create new business…
Tags: Advanced Analytics, AI, Artificial Intelligence, Business Agility, Customer Experience (CX)
“Time to Weed the Garden” – How CIOs Can Improve Customer Experience (CX)
Are companies making it difficult for our customers to use our products or consume the services we offer? Have they put business rules in place over time that now serve as barriers to delivering great customer experiences? As a consumer, you know the rules – the ones that constrain our options when we dare to…
Tags: Customer Experience (CX)
Cloud Security – Extending Your Cyber Fortress to the Cloud [White Paper]
Is your organization considering a move from on-premise systems to the cloud, but concerned about information security? Are you already using the cloud, but uncertain about how well your networks and data are protected? The transition to cloud computing is transforming businesses and IT departments worldwide, yet all too often, security is an afterthought. It…
Tags: Cybersecurity, Digital Transformation, IT Performance Improvement
Preparing to Become an Intelligent Enterprise: a Five-Tiered Approach
The fundamental distinction of the Intelligent Enterprise from its analog and digital predecessors is in the extensive use of data. While data is used today by businesses of all types, the sheer amount of data captured – both structured (e.g. databases) and unstructured (e.g. social media content) – is what is driving the Intelligent Enterprise….
Tags: Business Transformation
How to Avoid Extinction in the Age of Digital Disruptive Technology [White Paper]
Our latest white paper focuses on the urgent need for many companies to find their way from their current status struggling with legacy technologies to generating competitive advantages with emerging technologies like artificial intelligence and machine learning. Here are some clear warning signs that your organization is lagging behind and needs to move into a…
Tags: Artificial Intelligence, Business Transformation, Machine Learning
How to Avoid Extinction in the Age of Digital Disruptive Technology
If you’re trying to catch up with the digital economy while maintaining old, legacy systems and watching your competitors embrace digital transformation, machine learning, artificial intelligence and other emerging technologies, you may be running out of time. If you are concerned that you’re so far behind that your company’s survival is at stake, much like…
Tags: Digital Transformation
The Time to Invest in Cybersecurity is Not After a Breach
A major credit-reporting company recently disclosed that hackers possibly gained access to the personal information of 143 million US consumers, or roughly half the US population. In a statement made on the day of the public disclosure of the breach, the company’s chairman and CEO vowed to increase cybersecurity spending. Of course, this is the…
Tags: Cybersecurity